Introduction to Crypto Currency Market


Introduction to Cryptocurrency
Cryptocurrency is a type of digital or virtual currency that uses cryptography for security. Unlike traditional currencies issued by governments (such as the US dollar or euro), cryptocurrencies are decentralized and typically operate on a technology called blockchain, which is a distributed ledger enforced by a network of computers, or nodes.
Key Features of Cryptocurrency:
Decentralization: Cryptocurrencies are typically not controlled by any central authority, such as a government or financial institution. Instead, they rely on decentralized networks of computers to validate and record transactions.
Blockchain Technology: Most cryptocurrencies operate on blockchain technology, which is a secure, transparent, and immutable ledger that records all transactions across a network of computers. Each block in the chain contains a list of transactions, and new blocks are continuously added to form a chronological chain.
Cryptography: Cryptocurrencies use cryptographic techniques to secure transactions and control the creation of new units. This ensures the integrity and security of the data within the blockchain.
Anonymity and Pseudonymity: Transactions can be conducted with a certain degree of privacy. While transaction details are publicly visible on the blockchain, the identities of the individuals involved are often pseudonymous, meaning they are represented by alphanumeric addresses rather than personal information.
Digital Nature: Cryptocurrencies exist purely in digital form and are typically stored in digital wallets, which can be software-based (online, desktop, or mobile apps) or hardware-based (physical devices).
Uses and Applications:
Digital Payments: Cryptocurrencies can be used to make peer-to-peer payments without the need for intermediaries.
Investment and Speculation: Many people buy and hold cryptocurrencies as an investment, hoping their value will increase over time.
Decentralized Finance (DeFi): Cryptocurrencies are used in various DeFi applications, such as lending, borrowing, and trading, without traditional banks.
Smart Contracts: Self-executing contracts with the terms of the agreement directly written into code, primarily used on the Ethereum network.
Tokenization: The process of converting physical or digital assets into tokens that can be traded on a blockchain.
Cryptocurrencies are reshaping the financial landscape by providing new opportunities for innovation and inclusivity in the global economy. However, they also come with risks and challenges, such as regulatory uncertainty, price volatility, and security concerns. As the technology and its applications continue to evolve, understanding the basics of cryptocurrency is essential for anyone looking to engage with this transformative field.
History Of Bitcoin


Bitcoin
Bitcoin, the first and most well-known cryptocurrency, has a fascinating history that marks the beginning of the cryptocurrency revolution. Here’s a detailed overview of its development and significant milestones
Origins and Creation
Whitepaper Publication (2008):
In October 2008, an individual or group of individuals using the pseudonym Satoshi Nakamoto published a whitepaper titled "Bitcoin: A Peer-to-Peer Electronic Cash System." The paper outlined the concept of a decentralized digital currency that would allow for secure, direct transactions between parties without the need for intermediaries like banks.
Genesis Block (2009):
On January 3, 2009, Nakamoto mined the first block of the Bitcoin blockchain, known as the Genesis Block or Block 0. Embedded in the block was the text: "The Times 03/Jan/2009 Chancellor on brink of second bailout for banks," a reference to a headline in The Times newspaper, highlighting the financial instability that Bitcoin aimed to address.
Early Development and Adoption
First Bitcoin Transaction (2009):
The first transaction using Bitcoin occurred on January 12, 2009, when Nakamoto sent 10 bitcoins to cryptographic expert Hal Finney, marking the start of the Bitcoin network's operational use.
Bitcoin Pizza Day (2010):
On May 22, 2010, programmer Laszlo Hanyecz made the first real-world transaction by purchasing two pizzas for 10,000 bitcoins, a day now celebrated annually as Bitcoin Pizza Day.
Bitcoin Exchange Launches (2010):
The first Bitcoin exchange, BitcoinMarket.com, was established in March 2010, allowing users to trade bitcoins for traditional currencies. This was a significant step in Bitcoin’s path towards becoming a tradable asset.
Growth and Challenges
Mt. Gox and Early Price Surges (2011-2013):
Mt. Gox, one of the earliest and most popular Bitcoin exchanges, was launched in 2010 and became the largest Bitcoin exchange by 2011. Bitcoin's price experienced significant volatility, with notable surges, including reaching $1,000 for the first time in late 2013.
Regulatory Scrutiny and Silk Road (2011-2013):
Bitcoin gained attention for its use in illegal transactions, particularly on the Silk Road, an online black market. In 2013, the FBI shut down Silk Road and seized its assets, bringing Bitcoin into the spotlight for regulatory authorities worldwide.
Mainstream Recognition and Expansion
Mainstream Acceptance (2014-2017):
During these years, Bitcoin began to be accepted by a growing number of businesses, and investment in the cryptocurrency space surged. Major companies like Microsoft and Expedia started accepting Bitcoin for payments.
Forks and Scaling Debates (2017):
Bitcoin's popularity led to debates about its scalability. In August 2017, Bitcoin experienced a significant fork, resulting in the creation of Bitcoin Cash (BCH), which aimed to offer faster transaction times and lower fees.
Institutional Adoption and Modern Era
Institutional Investment (2018-2020):
Bitcoin saw increasing interest from institutional investors. Companies like MicroStrategy, Tesla, and Square made substantial investments in Bitcoin, and financial institutions began offering Bitcoin-related services.
Bitcoin's All-Time Highs (2020-2021):
Bitcoin's price reached new all-time highs, driven by institutional adoption, growing public awareness, and macroeconomic factors such as inflation concerns and monetary policy changes. It surpassed $20,000 in December 2020 and reached nearly $65,000 in April 2021.
Global Trends and Legal Tender (2021-Present):
In 2021, El Salvador became the first country to adopt Bitcoin as legal tender, marking a significant milestone in Bitcoin’s history. The cryptocurrency continues to evolve, with ongoing discussions about regulation, environmental impact, and technological improvements..
Legacy and Impact
Bitcoin has fundamentally transformed the financial landscape, introducing the concept of decentralized digital currency and sparking the development of thousands of other cryptocurrencies. It has paved the way for innovations in blockchain technology, decentralized finance (DeFi), and digital assets, influencing how we think about money and transactions in the digital age. Despite challenges and controversies, Bitcoin remains a pioneering force in the ongoing evolution of global finance.

Bitcoin Network
The Bitcoin network is a decentralized peer-to-peer system that enables the transfer and management of Bitcoin, a digital cryptocurrency. Here's an overview of its key components and how it operates:
Key Components:
Nodes:
These are computers that run Bitcoin software, validating and relaying transactions.
There are different types of nodes, including full nodes (which store the entire blockchain) and lightweight nodes (which do not store the full blockchain but rely on full nodes for data).
Blockchain:
A public ledger that records all Bitcoin transactions ever made.
It consists of a chain of blocks, with each block containing a list of transactions.
3.Miners:
Participants who use computational power to solve complex mathematical puzzles, a process known as proof-of-work.
Miners validate transactions and add new blocks to the blockchain, receiving newly created bitcoins and transaction fees as rewards.
Wallets:
Software applications or hardware devices that allow users to store, send, and receive bitcoins.
Each wallet contains one or more private keys, which are necessary for signing transactions.
Transactions:
Transfers of Bitcoin from one address to another.
Each transaction is verified by network nodes through cryptography and recorded on the blockchain.
How It Works:
Transaction Creation:
A user creates a transaction using a Bitcoin wallet, specifying the amount of Bitcoin to be sent and the recipient's address.
The transaction is broadcast to the Bitcoin network.
Transaction Validation:
Nodes validate the transaction by checking that the sender has enough balance and that the transaction follows Bitcoin protocol rules.
Valid transactions are then propagated through the network.
Mining:
Miners collect valid transactions from the network, compile them into a block, and begin solving the proof-of-work puzzle.
The first miner to solve the puzzle broadcasts the new block to the network.
Block Addition:
Nodes validate the new block and add it to their copy of the blockchain if it is valid.
This block becomes a permanent part of the blockchain, and the transactions within it are considered confirmed.
Consensus Mechanism:
Bitcoin uses a consensus mechanism known as proof-of-work to agree on the state of the blockchain.
The longest valid chain (the one with the most accumulated proof-of-work) is considered the true blockchain.
Security:
Cryptography:
Bitcoin relies on cryptographic techniques to secure transactions and control the creation of new units.
Decentralization:
The network's decentralized nature makes it resistant to censorship and centralized failures.
Incentives:
Miners are incentivized to act honestly through the reward system, which includes block rewards and transaction fees.
The Bitcoin network enables a trustless system where participants can transact without relying on intermediaries, such as banks or payment processors, making it a groundbreaking innovation in digital finance.
Hashing in Cryptocurrency
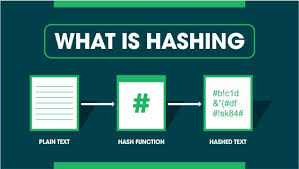
Hashing in cryptocurrency refers to the process of transforming an input (or "message") into a fixed-size string of bytes, typically a hash value or hash code, through a mathematical algorithm known as a hash function. In the context of cryptocurrencies like Bitcoin, hashing plays a crucial role in ensuring security, integrity, and the proper functioning of the blockchain. Here’s an in-depth look at hashing in crypto:
Key Concepts:
Hash Function:
A hash function is a mathematical algorithm that takes an input of any size and produces a fixed-size output, often represented as a hexadecimal number.
Common hash functions used in cryptocurrencies include SHA-256 (Secure Hash Algorithm 256-bit) and Keccak-256 (used in Ethereum).
Properties of Cryptographic Hash Functions:
Deterministic: The same input will always produce the same hash output.
Fast Computation: The hash value can be computed quickly for any given input.
Pre-image Resistance: It should be computationally infeasible to reverse-engineer the original input from its hash output.
Small Changes in Input: Any small change to the input should produce a significantly different hash (avalanche effect).
Collision Resistance: It should be extremely unlikely for two different inputs to produce the same hash output.
Puzzle Friendliness: The hash output should appear random and unpredictable.
Applications in Cryptocurrency:
Proof of Work (PoW):
In Bitcoin and other PoW-based cryptocurrencies, miners compete to solve a cryptographic puzzle. This puzzle involves finding a nonce (a random number) such that when it is added to the block's data and hashed using SHA-256, the resulting hash meets a specific condition (e.g., has a certain number of leading zeros).
This process secures the network by making it computationally expensive to alter the blockchain, thereby ensuring its integrity.
Blockchain Integrity:
Each block in the blockchain contains the hash of the previous block, forming a chain. This linkage ensures that any change in a block would alter its hash and break the chain, making tampering easily detectable.
Transaction Hashing:
Each transaction is hashed and included in a block. The hash ensures the integrity of the transaction data, preventing alterations.
Merkle Trees:
Transactions in a block are organized in a Merkle tree (or hash tree). Each leaf node is a hash of a transaction, and each non-leaf node is a hash of its child nodes. The root of the Merkle tree, known as the Merkle root, is included in the block header. This structure allows for efficient and secure verification of transactions within the block.
Address Generation:
Cryptocurrency addresses are often derived from the public key by hashing it (e.g., using SHA-256 followed by RIPEMD-160 in Bitcoin). This process helps to create shorter, fixed-length addresses from longer public keys.
Security and Efficiency:
Hashing ensures data integrity, authenticity, and security in the blockchain.
The computational difficulty of hashing puzzles in PoW provides security against attacks.
Efficient hashing algorithms enable quick verification and processing of transactions and blocks.
In summary, hashing is a fundamental cryptographic process in cryptocurrency systems, providing security, integrity, and efficiency in transaction processing, block creation, and overall blockchain maintenance.


Bitcoin mining
Bitcoin mining is the process by which new bitcoins are created and transactions are added to the blockchain. It involves using powerful computers to solve complex mathematical problems, which helps to secure the Bitcoin network and ensures the integrity of transactions. Here’s a detailed breakdown of how Bitcoin mining works:
Key Components of Bitcoin Mining:
Blockchain:
The blockchain is a public ledger that records all Bitcoin transactions. It consists of a chain of blocks, with each block containing a list of transactions.
Miners:
Miners are individuals or entities that use specialized hardware to participate in the mining process. They contribute their computational power to solve cryptographic puzzles.
Hash Function:
Bitcoin uses the SHA-256 (Secure Hash Algorithm 256-bit) hash function. Miners repeatedly apply this function to find a hash value that meets the network’s difficulty target.
Proof of Work (PoW):
PoW is the consensus mechanism used by Bitcoin. It requires miners to perform computational work to propose new blocks. The difficulty of this work ensures network security and integrity.
The Mining Process:
Transaction Collection:
Miners collect unconfirmed transactions from the Bitcoin network and bundle them into a candidate block.
Hash Calculation:
Miners begin by hashing the block header, which includes:
The previous block’s hash.
The Merkle root (a hash of all the transactions in the block).
A timestamp.
A nonce (a variable value that miners adjust).
Finding the Correct Hash:
Miners repeatedly hash the block header with different nonce values until they find a hash that meets the network’s difficulty target (i.e., the hash has a certain number of leading zeros).
This process is computationally intensive and requires significant processing power.
Block Validation:
Once a miner finds a valid hash, they broadcast the new block to the network.
Other miners and nodes in the network verify the block and the transactions it contains.
Block Addition:
If the block is valid, it is added to the blockchain, becoming the latest block in the chain.
The transactions within the block are considered confirmed.
Reward:
The miner who successfully mines a block is rewarded with newly created bitcoins (block reward) and transaction fees from the transactions included in the block.
The block reward halves approximately every four years (every 210,000 blocks) in an event known as the "halving." Initially, the reward was 50 bitcoins per block; it is now 6.25 bitcoins per block (as of 2020).
Importance of Bitcoin Mining:
Security:
Mining secures the Bitcoin network by making it difficult and costly to alter the blockchain. This ensures that the blockchain remains immutable and resistant to attacks.
Decentralization:
Mining is a decentralized process, meaning no single entity controls the network. This decentralization is a core principle of Bitcoin, promoting transparency and trust.
New Bitcoin Creation:
Mining is the mechanism by which new bitcoins are introduced into circulation. This controlled supply mechanism ensures a predictable and finite supply of bitcoins (capped at 21 million).
Mining Hardware:
CPU Mining:
Initially, mining was done using standard computer CPUs, but it is now impractical due to the high computational difficulty.
GPU Mining:
Graphics Processing Units (GPUs) provided more hashing power and were used as mining hardware after CPUs.
ASIC Mining:
Application-Specific Integrated Circuits (ASICs) are specialized hardware designed specifically for mining Bitcoin. They offer significantly higher efficiency and hashing power compared to CPUs and GPUs.
Environmental Impact:
Bitcoin mining consumes substantial amounts of electricity, leading to concerns about its environmental impact.
Efforts are being made to use renewable energy sources for mining to mitigate these concerns.
In summary, Bitcoin mining is the process by which transactions are validated and added to the blockchain, and new bitcoins are created. It involves solving complex cryptographic puzzles through computational work, ensuring the security and integrity of the Bitcoin network.


Blockchain Technology
At its core, a blockchain is a decentralized and distributed digital ledger that records transactions across many computers so that the record cannot be altered retroactively without altering all subsequent blocks and the consensus of the network.
Key Concepts and Components
Blocks:
Each block contains a list of transactions.
Blocks are linked together in a chronological order, forming a chain.
Transactions:
A transaction is a transfer of value (e.g., cryptocurrency) from one party to another.
Transactions are verified and recorded in blocks.
Hash Function:
A hash function takes an input (or "message") and returns a fixed-size string of bytes.
In blockchain, it ensures the integrity of the data. Any change in the input will produce a completely different hash.
Decentralization:
Unlike traditional ledgers that are maintained by a central authority (e.g., a bank), a blockchain is maintained by a distributed network of nodes (computers).
Consensus Mechanism:
A method used to achieve agreement on a single data value among distributed processes or systems. Examples include Proof of Work (PoW) and Proof of Stake (PoS).
Cryptography:
Cryptographic techniques secure data and control the creation of new units.
Public-key cryptography is commonly used, where each user has a public key and a private key.
How Blockchain Works
Initiating a Transaction:
A user requests a transaction, which is then broadcast to a network of nodes.
Each node has a copy of the blockchain and uses cryptographic algorithms to validate the transaction.
Transaction Validation:
Nodes validate the transaction using the sender’s public key and the transaction’s signature.
Valid transactions are gathered into a new block by miners (in PoW) or validators (in PoS).
Creating a New Block:
The new block contains a list of validated transactions, a timestamp, and the hash of the previous block.
This ensures all blocks are linked in the correct order.
Consensus and Block Addition:
Nodes reach a consensus to add the new block to the blockchain.
Once consensus is reached, the block is added to the blockchain, becoming a permanent part of the ledger.
Transaction Completion:
The transaction is confirmed, and the ledger is updated across all nodes.
The transaction is now complete and cannot be altered without changing all subsequent blocks, which would require consensus from the majority of the network.
Types of Blockchains
Public Blockchain:
Open to anyone to participate (e.g., Bitcoin, Ethereum).
Highly decentralized and transparent.
Private Blockchain:
Restricted access, typically within a single organization or group of organizations.
Offers more control and privacy but less transparency.
Consortium Blockchain:
Controlled by a group of organizations.
Balances decentralization and control, useful for business collaborations.
Applications of Blockchain
Cryptocurrencies:
The most well-known application, used for secure, peer-to-peer transactions (e.g., Bitcoin, Ethereum).
Supply Chain Management:
Enhances transparency and traceability of products.
Smart Contracts:
Self-executing contracts with terms directly written into code, executed when conditions are met (e.g., on Ethereum).
Voting Systems:
Ensures transparency and security in digital voting.
Healthcare:
Secure sharing of patient data among authorized parties.
Financial Services:
Streamlines cross-border payments and settlements.
Advantages of Blockchain
Decentralization:
Reduces the need for a central authority, minimizing single points of failure and censorship.
Transparency:
All transactions are publicly recorded and can be verified by anyone.
Security:
Cryptographic techniques ensure data integrity and authenticity.
Immutability:
Once recorded, data cannot be easily altered, ensuring the accuracy of the ledger.
Challenges of Blockchain
Scalability:
Processing large volumes of transactions quickly remains a challenge.
Energy Consumption:
Especially for PoW blockchains, mining can be energy-intensive.
Regulatory Uncertainty:
Governments are still figuring out how to regulate blockchain and cryptocurrencies.
Complexity:
The technology is complex and can be difficult to understand and implement correctly.
Getting Started with Blockchain
Education:
Learn about blockchain technology through online courses, articles, and books.
Wallets and Exchanges:
Set up a cryptocurrency wallet and use an exchange to buy and trade cryptocurrencies.
Development:
Experiment with blockchain development using platforms like Ethereum, which allows you to create and deploy smart contracts.
Join Communities:
Engage with blockchain communities, forums, and events to stay updated and connect with other enthusiasts.
Blockchain technology has the potential to revolutionize various industries by providing secure, transparent, and decentralized solutions. Understanding its fundamentals is the first step to exploring its vast possibilities.


Bitcoin Wallet
A Bitcoin wallet is a digital tool that allows users to store, manage, and conduct transactions with their Bitcoin. It is essential for interacting with the Bitcoin network, providing the interface through which users can send and receive Bitcoin, view their balance, and track transaction history.
Key Components:
Public Key: This is like an account number, used to receive Bitcoin. It is derived from the wallet's private key and can be shared openly.
Private Key: This is a secret number that allows the user to spend the Bitcoin associated with the corresponding public key. It must be kept secure.
Address: This is a shortened form of the public key, often represented as a string of alphanumeric characters or a QR code, used to receive Bitcoin.
Types of Bitcoin Wallets:
Hardware Wallets: Physical devices that securely store a user's private keys offline, protecting them from online threats. Examples include Ledger and Trezor.
Software Wallets: Applications that can be installed on a computer or mobile device. They store private keys and facilitate transactions. Examples include Electrum (desktop) and Mycelium (mobile).
Online Wallets: Web-based wallets accessible through browsers, hosted by third parties. They offer convenience but come with security risks, as the private keys are stored online. Examples include Blockchain.info and Coinbase.
Paper Wallets: Physical printouts of the public and private keys, often in the form of QR codes. They are secure from online attacks but can be lost or damaged.
Cold Storage: Refers to keeping Bitcoin completely offline, typically using hardware wallets or paper wallets, to prevent unauthorized access
Key Functions:
Send and Receive Bitcoin: Facilitates transactions by allowing users to input a recipient's address and the amount to be sent.
Balance and Transaction History: Displays the amount of Bitcoin held and a record of all transactions made.
Security Features: Includes encryption, multi-signature (requiring multiple private keys to authorize a transaction), and backup options.
Bitcoin wallets are crucial for securely managing Bitcoin, providing both a user-friendly interface and essential security features to protect the digital currency from theft and unauthorized access.
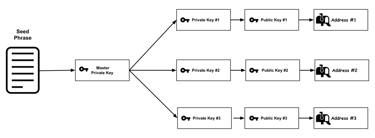
Seed Phrase
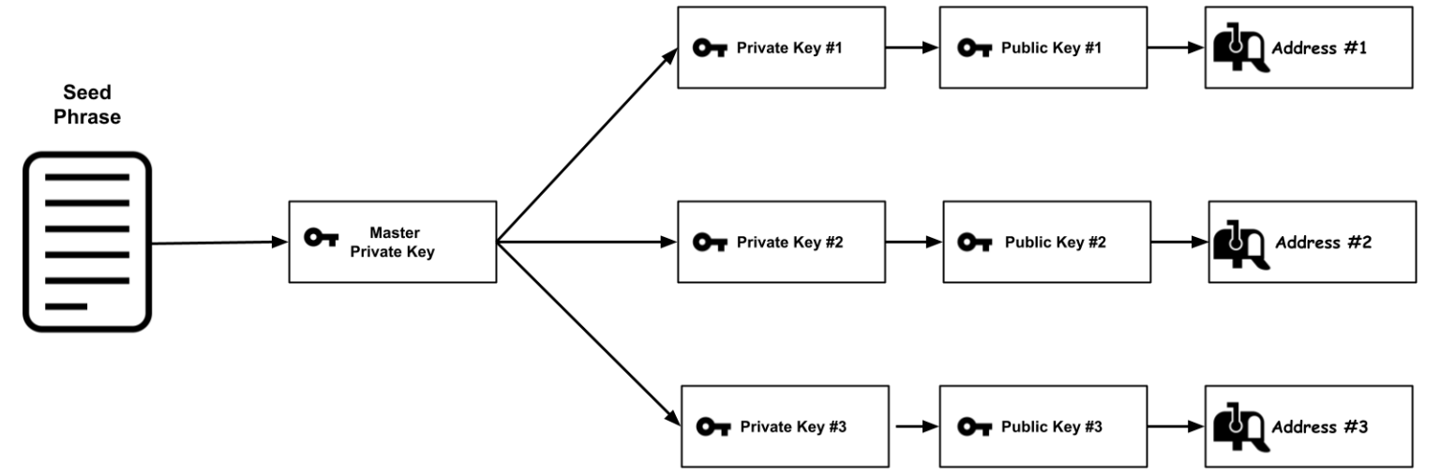
A seed phrase, also known as a recovery phrase, is a series of words generated by your cryptocurrency wallet that provides access to the wallet's private keys and, consequently, to your cryptocurrency holdings.
Key Features:
Mnemonic Phrase: Typically consists of 12, 18, or 24 words chosen from a predefined list of words (such as the BIP-39 standard word list).
Human-Readable: Designed to be easy to write down, read, and remember, unlike complex alphanumeric private keys.
Wallet Backup: Serves as a backup. If you lose access to your wallet (e.g., if your device is lost or damaged), you can recover your wallet and its funds by entering the seed phrase into a new wallet.
Security: As long as the seed phrase is kept secure and private, your funds are safe. Anyone with access to your seed phrase can access and control your funds.
How It Works:
Generation: When you set up a new wallet, it generates a seed phrase. This phrase is derived from a combination of random numbers and the wallet’s internal algorithm.
Restoration: To restore a wallet, the user inputs the seed phrase into the new wallet, which will then regenerate the same private keys and Bitcoin addresses.
Best Practices:
Write Down: Physically write down your seed phrase and store it in a secure, offline location. Avoid digital storage to protect against hacks and malware.
Multiple Copies: Consider creating multiple copies and storing them in different secure locations to safeguard against loss or damage.
Do Not Share: Never share your seed phrase with anyone. Treat it like the keys to your safe.
Examples of Usage:
Hardware Wallets: Devices like Ledger and Trezor prompt users to write down their seed phrases during setup.
Software Wallets: Apps like Electrum and Mycelium also generate seed phrases for backup purposes.
Example of a Seed Phrase:
correct horse battery staple
This simple string of words is actually a secure way to back up and restore your Bitcoin wallet. The strength lies in its randomness and length, making it extremely difficult for attackers to guess.
A seed phrase is a critical component of cryptocurrency security, enabling users to recover their funds even if their wallet is lost or damaged, provided they have securely stored their seed phrase.


Sending And Receiving Bitcoin
Sending and receiving Bitcoin involves using a Bitcoin wallet to manage your transactions. Here’s a step-by-step guide for both processes:
Sending Bitcoin:
Open Your Wallet: Access your Bitcoin wallet on your chosen platform (hardware, software, online, or mobile).
Initiate a Transaction:
Find the Send Option: Look for a button or tab labeled “Send” or something similar.
Enter Recipient’s Address: Input the recipient’s Bitcoin address. Double-check this address for accuracy, as transactions cannot be reversed.
Specify the Amount: Enter the amount of Bitcoin you want to send. Ensure the amount is correct.
Set the Transaction Fee: Most wallets allow you to set a transaction fee. Higher fees typically result in faster processing times.
Review and Confirm: Check all the details of your transaction. Confirm the recipient’s address and the amount.
Authorize the Transaction: Depending on your wallet, you may need to enter your password, use a hardware key, or provide other forms of authentication.
Send: Click the “Send” button. Your wallet will broadcast the transaction to the Bitcoin network for confirmation.
Receiving Bitcoin:
Open Your Wallet: Access your Bitcoin wallet on your chosen platform.
Find the Receive Option:
Locate Your Address: Look for a button or tab labeled “Receive” or similar. Your Bitcoin address will be displayed.
Generate a New Address: Some wallets allow you to generate a new receiving address for each transaction to enhance privacy.
Share Your Address: Copy your Bitcoin address and share it with the sender. You can also use the provided QR code if your wallet displays one.
Wait for Confirmation: Once the sender initiates the transaction, it will be broadcast to the Bitcoin network. You will typically receive a notification in your wallet when the transaction is confirmed.
Tips for Secure Transactions:
Double-Check Addresses: Always verify the recipient’s address to avoid mistakes.
Verify Amounts: Confirm the amount of Bitcoin being sent or received.
Monitor Network Fees: Be aware of current transaction fees and adjust accordingly for timely confirmations.
Use Trusted Platforms: Ensure you use reputable and secure wallets for managing your Bitcoin.


Digital Signature
In the context of cryptocurrency, a digital signature is a cryptographic technique used to ensure the authenticity and integrity of digital messages or transactions. It is a fundamental component of blockchain technology, providing security and trust without the need for a centralized authority
Key Concepts:
Public and Private Keys:
Private Key: A secret key known only to the user. It is used to sign transactions or messages.
Public Key: A key derived from the private key, used by others to verify the digital signature. It can be shared openly.
Digital Signature Process:
Signing: When a user wants to send a transaction, their private key is used to create a digital signature. This signature is unique to the transaction and the user’s private key.
Verification: Anyone with the sender's public key can verify the digital signature. This ensures the transaction was indeed signed by the owner of the private key and has not been altered.
How It Works:
Message Hashing: The transaction data (message) is hashed using a cryptographic hash function, producing a fixed-size string of characters (the hash).
Signature Creation: The hash is then encrypted with the sender’s private key, creating the digital signature.
Broadcasting: The signed transaction, along with the digital signature and the public key, is broadcast to the network.
Verification: Nodes in the network use the sender’s public key to decrypt the digital signature. If the decrypted hash matches the hash of the transaction data, the signature is valid, confirming the authenticity and integrity of the transaction.
Importance in Cryptocurrency:
Authenticity: Ensures that the transaction was created by the owner of the corresponding private key.
Integrity: Confirms that the transaction has not been tampered with since it was signed.
Non-Repudiation: Prevents the sender from denying that they initiated the transaction, as only they have access to the private key used to sign it.
Example in Bitcoin Transactions:
User A wants to send Bitcoin to User B.
Transaction Creation: User A creates a transaction specifying the amount of Bitcoin to send and User B’s address.
Digital Signature: User A’s wallet software hashes the transaction data and signs it with User A’s private key, creating a digital signature.
Broadcasting: The transaction, along with the digital signature and User A’s public key, is broadcast to the Bitcoin network.
Verification: Nodes in the network use User A’s public key to verify the digital signature. If the signature is valid, the transaction is added to the blockchain.
Digital signatures are a crucial aspect of cryptocurrency, enabling secure, transparent, and verifiable transactions within decentralized networks.


Altcoin
An altcoin is any cryptocurrency other than Bitcoin. The term "altcoin" is short for "alternative coin," indicating that these cryptocurrencies are alternatives to Bitcoin, which was the first and is the most well-known cryptocurrency.
Characteristics of Altcoins:
Diverse Features: While some altcoins aim to improve upon Bitcoin’s limitations (such as transaction speed and energy efficiency), others introduce entirely new features and use cases.
Varied Consensus Mechanisms: Altcoins can use different consensus mechanisms like Proof of Stake (PoS), Delegated Proof of Stake (DPoS), and Proof of Authority (PoA), in contrast to Bitcoin’s Proof of Work (PoW).
Smart Contracts and Decentralized Applications: Many altcoins, like Ethereum, enable the creation of smart contracts and decentralized applications (dApps).
Types of Altcoins:
Mining-Based Coins: These use Proof of Work (PoW) consensus mechanisms similar to Bitcoin. Examples include Litecoin and Monero.
Stablecoins: Cryptocurrencies pegged to the value of a stable asset, like fiat currency or gold, to minimize price volatility. Examples include Tether (USDT) and USD Coin (USDC).
Security Tokens: Digital assets that represent ownership or other rights to an asset, such as shares in a company. They are subject to federal securities regulations. Examples include tZERO and Polymath.
Utility Tokens: Provide access to a product or service within a specific platform or network. Examples include Basic Attention Token (BAT) and Filecoin (FIL).
Governance Tokens: Give holders voting rights within a blockchain project, allowing them to influence decisions about the project’s development and management. Examples include Maker (MKR) and Compound (COMP).
Notable Altcoins:
Ethereum (ETH): Known for its smart contract functionality and decentralized applications (dApps).
Ripple (XRP): Focuses on enabling fast and low-cost international money transfers.
Litecoin (LTC): Designed to provide faster transaction confirmation times than Bitcoin.
Cardano (ADA): Aims to create a more secure and scalable blockchain with a research-driven approach.
Polkadot (DOT): Enables interoperability between different blockchains.
Use Cases:
Payments: Some altcoins are designed to facilitate transactions and payments, similar to Bitcoin.
Smart Contracts: Platforms like Ethereum enable programmable contracts that execute automatically when certain conditions are met.
Decentralized Finance (DeFi): Many altcoins are used in DeFi applications, providing financial services like lending, borrowing, and trading without intermediaries.
Tokenization of Assets: Altcoins can represent ownership of real-world assets, such as real estate or art.
Risks and Considerations:
Volatility: Many altcoins are subject to significant price volatility.
Regulatory Risks: Regulatory frameworks for altcoins are still evolving, which can affect their adoption and legality.
Scams and Frauds: The altcoin market has been associated with scams and fraudulent projects. Due diligence is essential.
Altcoins expand the functionality and use cases of cryptocurrencies beyond what Bitcoin offers, contributing to the diversity and innovation within the blockchain and cryptocurrency space.
Privacy Coin
A privacy coin is a type of cryptocurrency that focuses on providing enhanced privacy and anonymity features for its users. Unlike traditional cryptocurrencies like Bitcoin, where transaction details are publicly available on the blockchain, privacy coins are designed to obscure transaction details to protect the identities of the parties involved and the amounts being transferred.


Key Features of Privacy Coins:
Anonymity: Ensures that the identities of the participants in a transaction are hidden.
Untraceability: Makes it difficult or impossible to trace the transaction history and link transactions to specific users.
Fungibility: Ensures that each coin is indistinguishable from another, which is important for the currency to be considered interchangeable.
Technologies Used in Privacy Coins:
Ring Signatures: Combine the sender’s signature with a group of others, making it difficult to identify the actual sender. Used by Monero.
Stealth Addresses: Generate one-time addresses for each transaction, hiding the recipient’s actual address. Also used by Monero.
Zero-Knowledge Proofs: Allow one party to prove to another that a statement is true without revealing any information beyond the validity of the statement. Used by Zcash (specifically, zk-SNARKs).
CoinJoin: Combines multiple transactions from different users into a single transaction, mixing the coins in a way that makes it difficult to determine which coins belong to which user. Used by Dash and other cryptocurrencies.
Notable Privacy Coins:
Monero (XMR): Known for its robust privacy features, including ring signatures, stealth addresses, and RingCT (Ring Confidential Transactions) which hide transaction amounts.
Zcash (ZEC): Offers the option of "shielded" transactions that use zk-SNARKs to hide sender, recipient, and transaction amount details.
Dash (DASH): Provides an optional privacy feature called PrivateSend, which uses CoinJoin to mix transactions.
Verge (XVG): Uses multiple anonymity-centric networks such as Tor and I2P to obfuscate IP addresses and transactions.
Grin (GRIN) and Beam (BEAM): Implement the Mimblewimble protocol, which provides privacy by default and focuses on scalability and confidentiality.
Use Cases:
Personal Privacy: Individuals who prioritize financial privacy and do not want their transaction history to be publicly accessible.
Commercial Transactions: Businesses that need to protect trade secrets or customer information.
Financial Sovereignty: Users in jurisdictions with restrictive financial regulations may use privacy coins to avoid surveillance and maintain economic freedom.
Risks and Considerations:
Regulatory Scrutiny: Privacy coins often attract attention from regulators and law enforcement due to concerns about their potential use in illegal activities such as money laundering and tax evasion.
Adoption Challenges: Exchanges and financial institutions may be hesitant to support privacy coins due to regulatory risks.
Technical Complexity: The advanced cryptographic techniques used in privacy coins can be complex, and vulnerabilities in implementation could potentially be exploited.
Example Monero Transaction:
Initiation: User A wants to send Monero to User B.
Ring Signature: User A’s wallet creates a ring signature, blending User A’s transaction with several others.
Stealth Address: User B’s wallet generates a one-time stealth address for the transaction.
Broadcast: The transaction, including the ring signature and stealth address, is broadcast to the Monero network.
Verification and Inclusion: Miners verify the transaction without knowing the actual sender or recipient and include it in a block.
Privacy coins provide enhanced anonymity and security features for users who prioritize financial privacy. While they offer significant benefits, they also face challenges related to regulation and adoption.
Meme Coins
A meme coin is a type of cryptocurrency that is often created as a joke or parody, typically based on a popular internet meme or cultural phenomenon. Unlike traditional cryptocurrencies like Bitcoin or Ethereum, which are designed with specific technological goals and use cases in mind, meme coins primarily gain value and popularity through social media hype, community engagement, and internet trends.


Characteristics of Meme Coins
Origin:
Typically started as a joke or a parody.
Inspired by popular internet memes or cultural phenomena.
Community-Driven:
Heavily reliant on social media hype and community engagement.
The value often fluctuates based on online trends and viral campaigns.
Volatility:
Prone to extreme price volatility.
Prices can skyrocket rapidly due to viral interest and drop just as quickly.
Low or No Utility:
Often lack significant utility or technical innovation.
The primary appeal is the novelty and community involvement.
Examples of Popular Meme Coins
Dogecoin (DOGE):
Created in 2013 as a parody of the cryptocurrency craze.
Inspired by the popular "Doge" meme featuring a Shiba Inu dog.
Gained mainstream attention and significant market capitalization due to endorsements from celebrities and internet influencers.
Shiba Inu (SHIB):
Launched in 2020 as an experiment in decentralized community building.
Dubbed the "Dogecoin killer," aiming to replicate and surpass the success of Dogecoin.
Developed a large and active community quickly.
Pepe Coin (PEPE):
Based on the "Pepe the Frog" meme.
Known for its humorous and sometimes controversial origins.
Reflects the speculative and community-driven nature of meme coins.
Risks and Considerations
High Risk:
Investments in meme coins can be highly speculative and risky.
Prices are susceptible to pump-and-dump schemes.
Regulatory Concerns:
Regulatory scrutiny may affect the legality and future of meme coins.
Potential for scams and fraudulent activities.
Market Sentiment:
Value is heavily influenced by market sentiment rather than intrinsic value.
Changes in public interest can cause rapid price changes.
Conclusion
Meme coins represent a unique intersection of cryptocurrency and internet culture. While they can offer significant short-term gains, they also come with high risks and uncertainties. Investors should approach meme coins with caution, thoroughly researching and understanding the inherent volatility and speculative nature of these digital assets.


Stablecoins
Stablecoins are a type of cryptocurrency designed to maintain a stable value relative to a specific asset or a basket of assets, typically a fiat currency like the US Dollar or a commodity like gold. They aim to combine the benefits of cryptocurrencies (such as fast transactions and security) with the stability of traditional financial systems.
Characteristics of Stablecoins
Pegged Value:
Stablecoins are pegged to a stable asset, such as USD, EUR, or gold, maintaining a 1:1 ratio or other fixed rate.
This peg helps reduce volatility, making them more reliable for transactions and storing value.
Backed by Reserves:
Many stablecoins are backed by reserves of the asset they are pegged to. For instance, a USD-backed stablecoin should have USD reserves equivalent to the number of coins in circulation.
Transparent and Auditable:
To build trust, stablecoin issuers often provide transparency about their reserves through regular audits by independent third parties.
Types of Stablecoins
Fiat-Collateralized Stablecoins:
Backed by fiat currency reserves held in a bank.
Examples: Tether (USDT), USD Coin (USDC), Binance USD (BUSD).
Crypto-Collateralized Stablecoins:
Backed by other cryptocurrencies held in smart contracts.
Typically over-collateralized to account for the volatility of the backing crypto.
Example: DAI, backed by Ethereum and other cryptocurrencies.
Commodity-Collateralized Stablecoins:
Backed by reserves of physical assets like gold or real estate.
Examples: PAX Gold (PAXG), Digix Gold (DGX).
Algorithmic Stablecoins:
Maintain their peg through algorithms and smart contracts that control the supply of the stablecoin.
Use mechanisms like minting and burning tokens to maintain price stability.
Example: TerraUSD (UST), although it's important to note that some algorithmic stablecoins have faced stability issues.
Use Cases
Trading and Hedging:
Used to hedge against the volatility of other cryptocurrencies.
Serve as a stable medium for trading on cryptocurrency exchanges.
Remittances and Payments:
Facilitate low-cost and fast cross-border transactions.
Provide a stable means of payment for goods and services in regions with unstable fiat currencies.
Decentralized Finance (DeFi):
Integral to many DeFi protocols, used for lending, borrowing, and yield farming.
Provide liquidity in decentralized exchanges (DEXs).
Savings and Investments:
Used as a stable store of value.
Offer interest-bearing accounts on various DeFi platforms.
Advantages
Stability:
Reduced price volatility compared to traditional cryptocurrencies.
Provides predictability for transactions and investments.
Accessibility:
Easier for everyday use and adoption by businesses.
Simplifies the process of entering and exiting the crypto market.
Speed and Efficiency:
Enables fast and cost-effective transfers, especially in cross-border payments.
Risks and Considerations
Regulatory Risks:
Subject to regulatory scrutiny and potential changes in regulation.
Concerns about the legitimacy and sufficiency of reserves.
Centralization:
Some stablecoins, especially fiat-collateralized ones, are centralized, which goes against the decentralized ethos of cryptocurrencies.
Reliance on trust in the issuing entity.
Technical Risks:
Algorithmic stablecoins are susceptible to smart contract failures or market manipulation.
Crypto-collateralized stablecoins depend on the stability of their underlying assets.
Conclusion
Stablecoins play a crucial role in the cryptocurrency ecosystem by providing stability, facilitating transactions, and enabling participation in the DeFi space. While they offer numerous benefits, users should be aware of the associated risks and choose stablecoins backed by reputable entities with transparent operations.
